“Onions have layers. Ogres have layers. Onions have layers. You get it? We both have layers.”
– Shrek

PART TWO
PART TWO
Ogres are Like Onions, and So is Good Data Security
Ogres are Like Onions, and So is Good Data Security
In our last Knowledge Burst (Time For Secure Cloud Data), we explored the different vulnerabilities hidden within traditional cloud storage environments. Now, it’s time to roll up our sleeves and counterattack the threats lurking in the shadows.
Who doesn’t love Shrek and his depth of character, declaring his complex nature? Much like this loveable character, I implore you to be an onion — well, your data security, at least.
Businesses need a layered security approach, with each layer serving as a formidable line of defense. Layered security concepts aren’t new, but how we build and manage them must adapt at an ever-accelerating pace. To do so, we must address each layer that we use to build our data ecosystems.
In our last Knowledge Burst (Time For Secure Cloud Data), we explored the different vulnerabilities hidden within traditional cloud storage environments. Now, it’s time to roll up our sleeves and counterattack the threats lurking in the shadows.
Who doesn’t love Shrek and his depth of character, declaring his complex nature? Much like this loveable character, I implore you to be an onion — well, your data security, at least.
Businesses need a layered security approach, with each layer serving as a formidable line of defense. Layered security concepts aren’t new, but how we build and manage them must adapt at an ever-accelerating pace. To do so, we must address each layer that we use to build our data ecosystems.
In our last Knowledge Burst (Time For Secure Cloud Data), we explored the different vulnerabilities hidden within traditional cloud storage environments. Now, it’s time to roll up our sleeves and counterattack the threats lurking in the shadows.
Who doesn’t love Shrek and his depth of character, declaring his complex nature? Much like this loveable character, I implore you to be an onion — well, your data security, at least.
Businesses need a layered security approach, with each layer serving as a formidable line of defense. Layered security concepts aren’t new, but how we build and manage them must adapt at an ever-accelerating pace. To do so, we must address each layer that we use to build our data ecosystems.
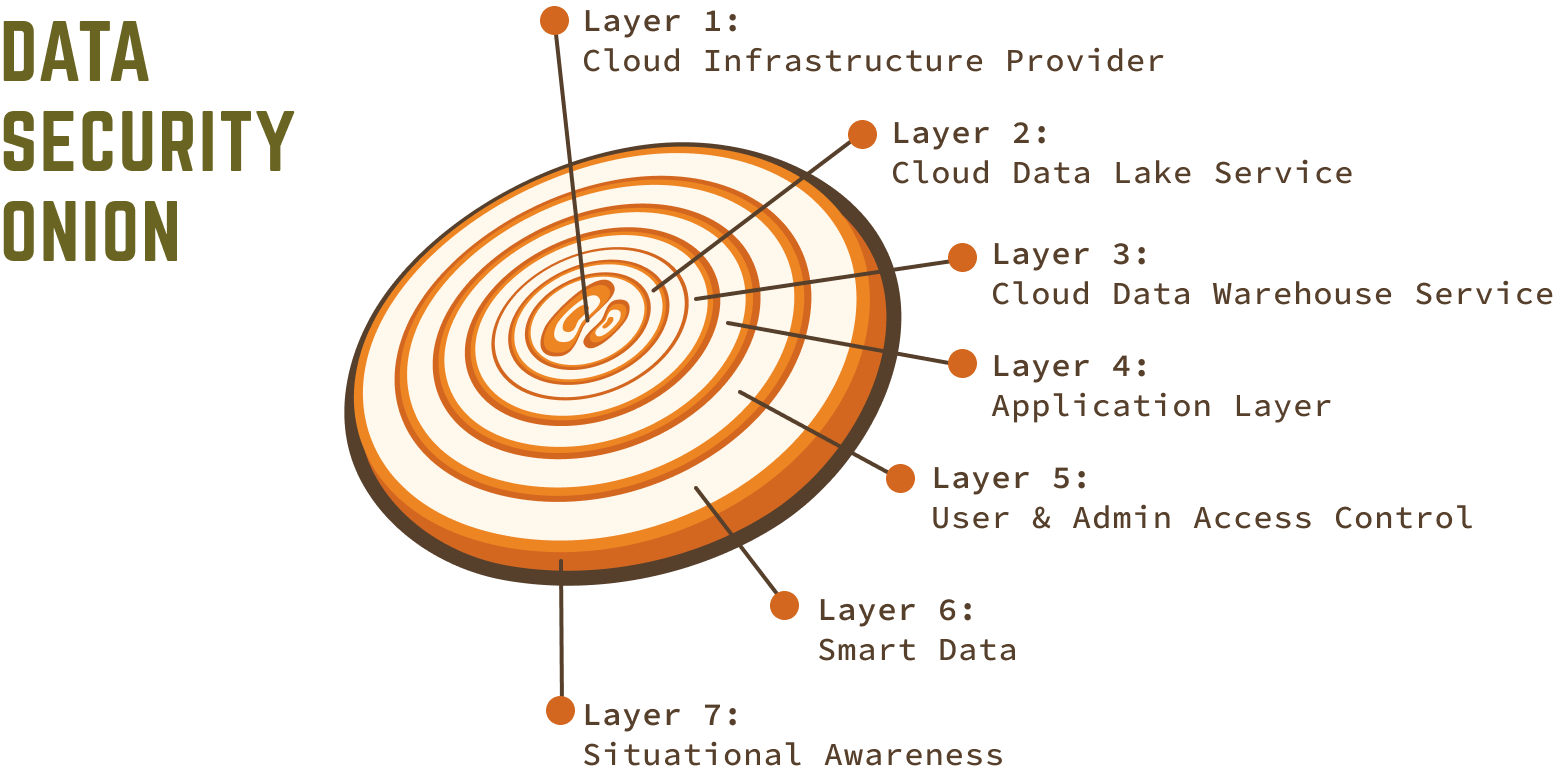
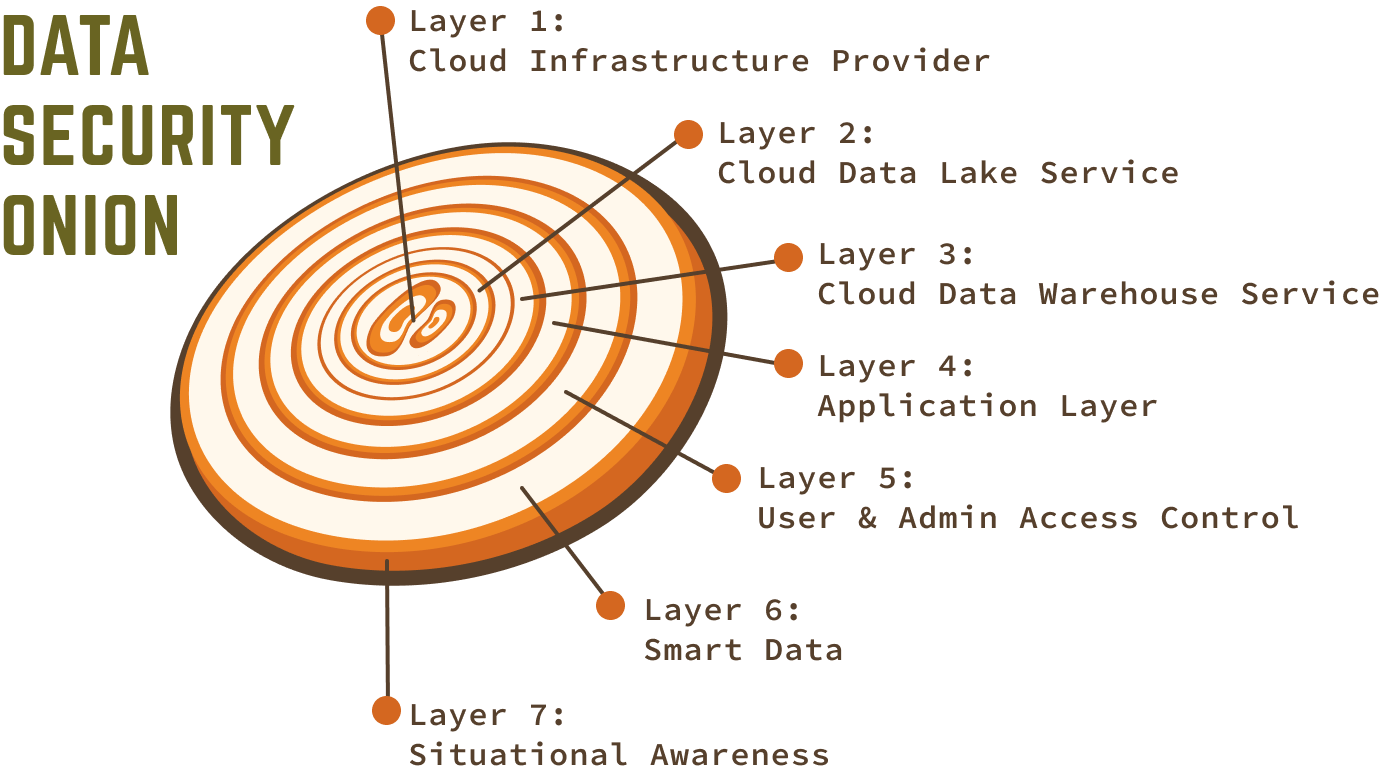
Data Security Onion
The Sturdy Foundation
Layer 1: Cloud Infrastructure Provider
Just like a house needs a strong foundation, your cloud data solution requires a secure infrastructure. The cloud infrastructure provider is responsible for the physical and network security of the data centers, implementing measures such as surveillance, access controls, and robust network security protocols to keep the bad guys out. Examples include Google Cloud, Microsoft Azure, AWS.
The Watchful Guardian
Layer 2: Cloud Date Lake Service
Cloud data lake services act as the watchful guardians of your data. They must implement data encryption, access controls, and secure data ingestion processes to ensure that your data remains protected, both at rest and in transit. By extension, they must also provide the tooling for customers to extend, manage, and even customize these services.
The Query Guardian
Layer 3: Cloud Data Warehouse Service
Data warehouses focus on securing query processing and data storage, using strong encryption, auditing access logs, and integrating with other security layers to create a shield around your data.
The Gatekeeper
Layer 4: Application Layer
Applications that access your cloud data are like the gates to your fortress. They must be secured to prevent vulnerabilities like SQL injection and cross-site scripting. Implementing secure coding practices like those found in OWASP’s open-source security initiatives and regular security assessments helps keep these gates firmly locked. No matter how good the security of the underlying layers may be, it can all be circumvented here.
The Key Master
Layer 5: User & Admin Access Control
Robust access management is like having a trusted key master. Techniques like multi-factor authentication (MFA) and role-based access control (RBAC) ensure that only authorized users have the keys to your kingdom. When we work with our customers, we highly discourage any one individual or small group of individuals from having “super user” privileges to all aspects of the system, including data access. You should ask questions like, “Do most cloud engineers require unconditional access to organizational data?” and “Does a data scientist need to have system administration privileges?”
I think it’s safe to say all of the above are simply table stakes regarding data security. To truly take security to the next level, we have to move beyond secured databases to the next level of embedding security into the data itself.
The Art of Self-Defense
Layer 6: Smart Data
Smart data injects a new layer of security into the data itself. Each data asset is cryptographically signed, making the data itself, not just the database, secure. With smart data, your data is promoted to black belt status. I’ll dive deeper into smart data below.
Smart People
Layer 7: Situational Awareness
Finally, you have to arm your business with a team of professionals who are dedicated to a comprehensive understanding of your organization’s environment and potential threats. They must constantly be alert to identify vulnerabilities, detect anomalies, respond effectively to incidents, improve risk assessment, and enhance decision-making processes.
Privacy Enhanced 101
The Difference Between PETs/PECs/PEDs
One of the first Knowledge Bursts in this series was titled How You Handle Data Privacy Will Determine If You Win Or Lose In a Web3 World. The whole premise of this blog is that we need to think about data security from a whole new perspective. One that sees the data landscape not as a lake, ocean, or warehouse but as an ecosystem of interconnected players, none of whom own and control all the data they need. I will touch on concepts contained in this blog, but I suggest that you re-read it for greater context. Let’s dive in.
Privacy-Enhanced Technology and Computing: Old School with a Twist
In the world of cloud data security, privacy-enhanced technology (PET) and privacy-enhanced computing (PEC) are like a magical invisibility cloak that keeps your sensitive data hidden from prying eyes. These technologies include techniques like homomorphic encryption, which allows computations on encrypted data without revealing its contents, and secure multi-party computation, which enables collaborative data analysis without exposing individual data points.
As veterans in the privacy and cybersecurity space, we believe the current generation of PET/PEC is fast approaching its event horizon. While some technical advances may slightly extend the lifespan of legacy PET/PEC systems, there exists a fundamental flaw in the underlying premise: legacy PET/PEC systems assume that data is dumb. As such, they take a very traditional systems approach to data protection: controlling access to the database, where and how the data may be processed, and standard encryption techniques to hide sensitive information such as identity.
But data isn’t dumb anymore. Or at least, it doesn’t need to be. Next-generation PET and PEC are moving towards a more data-centric approach that uses what we’ll call “Privacy Enhanced Data.” In the BurstIQ ecosystem, we call this smart data.
Privacy Enhanced Data – The Smart Way to Go
Enter BurstIQ with the plan to revolutionize privacy-enhanced data management. With our smart data solutions, BurstIQ harnesses the power of blockchain technology and advanced encryption to create an impenetrable shield around your data transactions.
Privacy Enhanced Data (PED), also known as smart data, represents the future of data privacy and intelligence. It combines various data attributes like metadata, edge relationships, ownership, user permissions, and consent into a cryptographically signed and attested data object. Think of it as self-aware data.
By integrating these attributes into the data itself, the smart data object gains intelligence. Embedded attributes like metadata and edge relationships provide context, allowing real-time configuration and driving the behavior of processing systems. This dynamic approach outperforms traditional models, enabling rapid learning, adaptation, and optimization in the face of explosive data growth and the demand for deep intelligence.
Beyond context, smart data objects include trust attributes. Ownership and use permissions are embedded and enforced within the data, ensuring data security during movement and replication. Trust attributes also offer a comprehensive audit trail, tracking changes, ownership, permissions, and authentication by trusted entities.
With trust attributes embedded within the data, smart data addresses the challenge of data integrity and privacy. Permission revocation becomes a standard feature, empowering organizations to maintain control.
The significance of smart data lies in its ability to liberate data from central control systems. Data security and intelligence become mobile, allowing seamless sharing, replication, and updates without compromising integrity, security, or intelligence required for business operations. BurstIQ paves the way for a new era of privacy-enhanced data management.
BurstIQ’s approach is like having a digital bodyguard that ensures your data remains private and tamper-proof, no matter where it travels. This is particularly crucial in distributed data management, where secure data sharing and collaboration across different platforms and stakeholders are essential.
By integrating privacy-enhanced data techniques, BurstIQ is a robust solution for securing existing cloud data solutions like Snowflake, addressing key security concerns and paving the way for a more secure and trustworthy data future.
Conclusion
Embracing the Secure Data Revolution
In the ever-evolving landscape of cloud data solutions, security is not just an option – it’s a necessity. By understanding the vulnerabilities that threaten our data and embracing the power of layered security measures and privacy-enhanced technologies, we can build a future where our data is not only accessible and insightful but also secure and private.

In the ever-evolving landscape of cloud data solutions, security is not just an option – it’s a necessity. By understanding the vulnerabilities that threaten our data and embracing the power of layered security measures and privacy-enhanced technologies, we can build a future where our data is not only accessible and insightful but also secure and private.
In the ever-evolving landscape of cloud data solutions, security is not just an option – it’s a necessity. By understanding the vulnerabilities that threaten our data and embracing the power of layered security measures and privacy-enhanced technologies, we can build a future where our data is not only accessible and insightful but also secure and private.
As we move forward, it’s crucial for organizations to prioritize regular security audits, invest in advanced security technologies, train employees, and continuously update security policies to stay one step ahead of the bad guys.
The story of cloud data security is one of heroes and villains, of challenges and triumphs. By arming ourselves with knowledge, innovation, and a commitment to protecting our valuable data, we can all become the heroes of our own data security tales.
So, let’s raise our shields, unleash our inner data defenders, and embrace the secure data revolution together!

About BurstIQ:
BurstIQ’s LifeGraph is an advanced data management platform that enables secure, transparent, and efficient data management for businesses across various industries. By harnessing the power of blockchain technology, BurstIQ empowers organizations to quickly integrate data from any source so they can create a trustworthy business ecosystem. The platform applies knowledge graphs to make data more accessible and to deliver insights that optimize processes, reduce risk, and personalize customer solutions across their ecosystems. With a strong focus on innovation and customer-centricity, BurstIQ continues revolutionizing industries and setting new standards in enterprise blockchain-powered Web3 solutions.